Creating a centralized exchange or CEX, is a business project that can drive a lot of profit. But these platforms often become prime targets for cybercrime. Recent cryptohacks at ByBit in 2025 (~$1.4-1.5 billion stolen), BingX in 2024 (~$43-44 million stolen), and other centralized well-known platforms highlight the importance of strong security measures.
A secure and safe CEX is a reality, but developers must deploy a multi layer security model (defense-in-depth, in other words). Why? Because this approach involves the application of independent, multiple security controls in every aspect of the CEX system, from user authentication security to wallet custody and real-time monitoring.
Is your crypto exchange secure enough to stop hackers? In this article, we will analyze each vital security tier, consider best practices, and explain how to implement them for a secure and compliant CEX.
What is multi-layer security in the context of CEX?
Multi layer security is a cybersecurity strategy that is built on several independent layers of defenses to secure systems, data, and users. For a CEX, security should be integrated into every level of the platform – from frontend user interfaces to backend infrastructure and blockchain integrations.
It is not enough to rely on a single layer (for example, just a firewall). A multi-layered security ensures that even if one defense of the exchange is compromised, other tiers remain in place to protect the platform and users.
Each layer of security guards your crypto venture against a specific attack vector or threat surface:

All these layers combine to form an unbreakable shield for your crypto exchange that is stronger than each component separately.
Why a layered approach to security matters for CEXs
These crypto exchanges are at risk of a wide range of attacks, each one aimed at a different part of the platform. From hijacked user accounts to crypto wallet phishing, attackers are always looking for loopholes. That’s why a layered solution is necessary.
So, what attacks does this approach help protect against?
For example, the multi-tier security approach helps to stop password cracking and phishing attacks targeting user accounts.
In a multi-layer strategy, even if a login is hacked by an attacker, additional tiers (withdrawal confirmation, wallet-level multisignature controls) prevent transfers of funds. Did you know that in 2024, phishing scams stole over $46M in just 1 month? The hackers tricked users into revealing their private credentials and signing diverse malicious transactions.
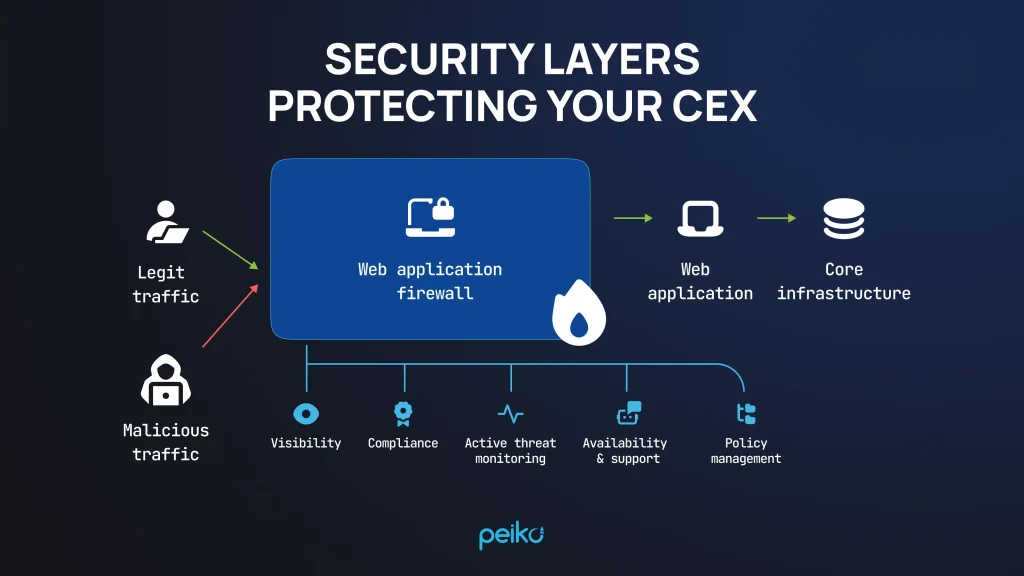
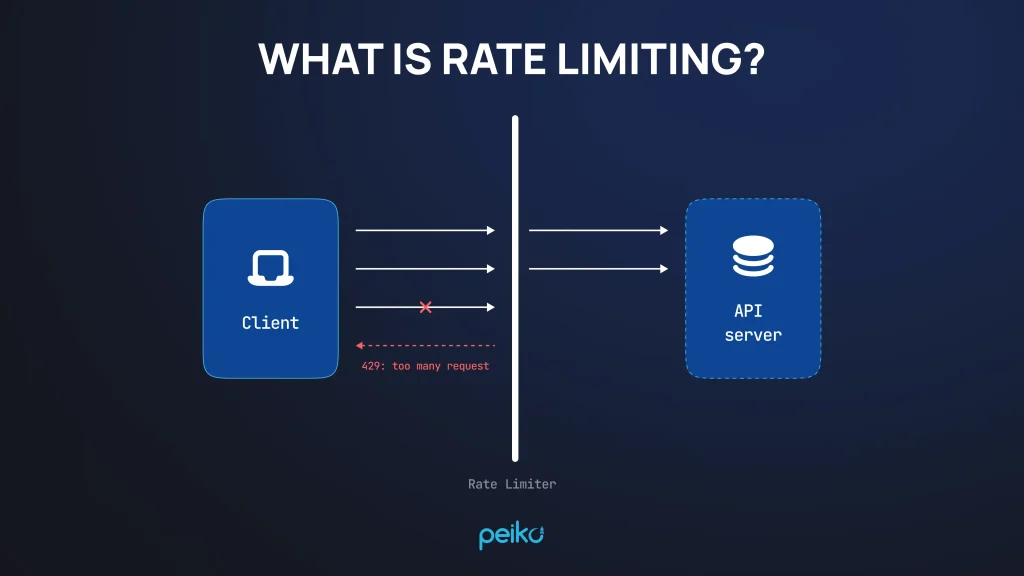
APIs and application layers are also quite vulnerable to hacker attacks. Here, you need robust WAFs and rate limiting to protect these parts of the platform by denying malicious requests and detecting any suspicious activity.
DDoS attacks try to flood the exchange with fake traffic to take it offline. This can scare your users off as well as cause financial loss. With layered protection against hacks, like traffic filters and auto-scaling servers, the site stays online even during severe attacks.
Large crypto balances are another favorite target. The use of cold storage, multisignature wallets, and HSMs is a strong security layer, whereby it is quite difficult for hackers to steal money. (In July 2024, WazirX suffered a $235M wallet breach involving a compromise in multisig wallet approval mechanisms)
Data breaches that expose sensitive user information can lead to legal issues and reputation loss. So, data encryption at rest and in transit is another worthwhile layer of security.
| Attack type | Target area | Multi-tier defense examples | Risk if unprotected |
| Phishing / сredential theft | User accounts | 2FA, login alerts, withdrawal confirmations | Unauthorized access, fund withdrawal |
| DDoS attacks | Network / Server availability | Traffic filtering, DDoS mitigation tools, autoscaling | Downtime, user loss, interruptions during trading |
| Wallet hacks | Custody / Assets | Cold storage, HSMs, multisig wallets | Loss of large amounts of crypto |
| Data breaches | User data / database | Data encryption (at rest & in transit), access control | User privacy violations, legal consequences |
The elements of multi-layered security for CEX platforms
The classical defense-in-depth model in CEX environments comprises the following principal components:
Infrastructure segmentation and zero trust: Micro-segmentation of the network and the “never trust, always verify” rule limits possible damage even if an account or node is breached to some degree.
HSM and multi-party computation (MPC): Private key protection is enforced using hardware security modules and increasingly using MPC protocols, security and availability being maintained without single points of failure.
Identity and access management (IAM) frameworks: Modern IAM products with support for ephemeral tokens (temporary access tokens), audit trails, just-in-time (JIT) access, and contextual authentication secure and minimize access risk.
Runtime security and exploit protection: Through the use of runtime application self-protection (RASP), behavioral analysis, sandboxing, and runtime attack protections (such as remote code execution or privilege escalation).
Continuous monitoring and DevSecOps: Security integrated across the CI/CD pipeline, static and dynamic code scanning automatically, and runtime protections in production.
Below, we will consider how all these elements relate to the multi-layered security model commonly utilized by top CEX platforms.
The layered security model: How it works
This security model for CEX platforms takes a defense-in-depth approach by segmenting security controls into seven layers. Each of these layers counters unique threats and integrates to prevent breaches:
User layer
This first line of defense authenticates users using multi-factor authentication (MFA), adaptive risk scoring, and behavioral analytics. It resists phishing, credential stuffing, and insider threats by authenticating identity and monitoring account activity. This layer is established on the IAM frameworks described above.
Application layer
In this, security controls protect software stack, web interfaces, and APIs by means of hardened configurations, WAFs, rate limiting, and runtime defense such as RASP to prevent OWASP Top 10 threats and abuse attempts.
Network layer
The perimeter of the infrastructure is secured using next-generation firewalls (NGFW), intrusion detection and prevention systems (IDS/IPS), segmentation of networks (complementary to infrastructure segmentation in the first section), and DDoS protection. These measures prevent attackers from easily accessing critical systems or being able to move laterally once inside.
Data layer
Data confidentiality and data integrity are protected using encryption methods (AES-256, TLS 1.3), tokenization of PII, and strict key management policies, such that personally identifiable information (PII) and transactions are not revealed.
Wallet layer
Private keys are secured through a blend of HSMs and sophisticated MPC protocols (as discussed in the key elements). This layer enforces hot, warm, and cold wallet separation, automating asset transfers to limit exposure and prevent unauthorized use.
Monitoring layer
Integrated security information and event management (SIEM) systems, machine learning-based behavioral anomaly detection, and automated alerts come together to provide rapid detection and response to suspicious activity or potential breaches. This is in line with the above-discussed continuous monitoring and DevSecOps procedures.
Compliance layer
To establish compliance, it is essential to conduct automated regulatory checks, audit trails, and integrate reporting mechanisms. This will help you ensure the platform is compliant with global regulatory standards and internal guidelines, reducing risk and building user trust.
Challenges in implementing a multi layer security strategy
Building a robust, multi-layered security infrastructure in a CEX environment is a task for professionals. The complexity of integrating disparate technologies and business processes creates a number of challenges:
System integration / interoperability
The systems of CEXs are usually designed of disparate components: third-party custodians, proprietary microservices. If you want to support seamless and full-covered secure communication between these layers without creating zones of vulnerability, you need sophisticated design and continuous testing.
Balancing security and performance
High-end cryptographic protection capabilities (for example, MPC, HSM) and real-time behavioral monitoring cause latency. Maintaining fast, fluid user interactions in high-frequency trading use cases with rigorous security constraints requires precision optimization.
Emerging threat environment
The methods of attackers evolve. New vulnerabilities keep being discovered. Maintaining each layer of security to be up to date with new threats requires investment in penetration testing, adapting defenses, and other security measures.
Human factor / insider risk
Employee failure remains one of the main issues even with high-quality technical controls. To reduce the risk of phishing, misconfiguration, and malicious insiders demand strict access governance, continuous security awareness training, and modern zero-trust tactics.
Regulatory complexity
Cross-border trading operations should be compliant with regulatory regimes (AML/KYC, ISO standards, GDPR). It is essential to implement management of multi-layered security controls and compliance needs.
To deal with all these challenges, you need a strategic security approach, combined with automation, real-time monitoring, and a security-focused culture.
Best practices for a strong layered defense in CEX platforms
Implementing layered protection on a centralized exchange is not a one-time project, but a whole lifecycle that evolves in accordance with changes in threats, infrastructure, and user behavior. To achieve a full-fledged CEX with operational resilience, we recommend following a series of best practices that bring technology and governance into harmony:
- Threat modeling by layer Do systematic threat modeling (STRIDE, MITRE ATT&CK models) across all layers — user, app, network, data, wallet, monitoring, and compliance. This will help identify potential points of entry and abuse vectors.
- Key material isolation Isolate cryptographic operations stringently. Use MPC for transaction auth, HSMs – for cold storage. Also, eliminate key exposure between environments (even dev/test).
- Granular IAM and policy enforcement Move past simplistic RBAC or role-based access control. You may use attribute-based access control (ABAC), and least privilege enforcement, context policies (geo-IP blocking, time-of-day access).
- Security automation in CI/CD Adopt DevSecOps discipline. This means integrating SAST (static application security testing), DAST (dynamic application security testing), and also dependency scanning into pipelines. Furthermore, ensure security gates are enforced before pushing into production.
- Live incident response playbooks Develop dynamic response playbooks that are embedded in SIEM (security information and event management)/SOAR (security orchestration, automation, and response) tools. Automate initial actions (account freezing, wallet circuit-breakers) on pre-configured triggers.
- End-to-end observability Means having full visibility across all the exchange’s infrastructure, applications, transaction flows, and user sessions. To detect complex, multi-stage attacks, connect and correlate data across all these areas.
- Security-first culture Provide security teams with budgetary and decision-making authority. It is also important to ensure ongoing development, ops, and support team training on crypto-native threats like smart contract attacks, wallet theft, and social engineering.
Ultimately, layered protection must not just reduce risk but scale with the business — in terms of performance and compliance.
Want to implement these best practices on day one? At Peiko, we’ve already made this multi-layered approach a part of our white-label crypto exchange platform. You can launch in as few as 3 weeks, with a platform having enterprise-grade protections out of the box.
These protections include 2FA-secured user login and withdrawal, Fireblocks custody integration, autoscaling infrastructure for traffic spikes, encrypted data storage, isolated modular microservices, and battle-tested DDoS resilience.
If you want to start a crypto exchange, we can get it done faster, securely, and horizontally scalable.
Future of multi-tier defense in CEX
As the threat landscape becomes more sophisticated and the regulatory spotlight on digital asset platforms intensifies, layered protection is transitioning from a best practice to a core market differentiator. Here’s where we’re headed:
MPC Infrastructure-as-a-service is the new standard: Fireblocks, Zengo X, and Curv are paving the way with MPC-as-a-Service. MPC-based processes will soon be table stakes for institutional-level custody and real-time asset processing — especially to meet standards like ISO 27001 and SOC 2 in the future.
Adaptive security on AI (artificial intelligence)/ML (machine learning): The use of AI helps to add behavioral modeling and threat detection in security stacks. These features will assist in identifying session anomalies, deviation in transaction patterns, or misuse of APIs in real-time. Chainalysis Reactor, Paladin AI, Fortanix Confidential AI, are certain projects that show the great potential of using AI, ML solutions for enhanced protection.
Wallet policy management via APIs: Cold, warm, and hot wallet management is being brought together into programmable policy engines. Anchorage, Ledger Enterprise, and GK8 platforms are pushing exchanges to APIs that allow exchanges to apply transaction approvals, delays, velocity caps, and on-chain compliance rules by wallet.
Secure compute (TEE, confidential virtual machines): TEE or trusted execution environments (Intel SGX, AMD SEV) and confidential cloud infrastructure will soon be able to host segments of exchange logic (order books, transaction queues) independently from the host OS, and protect against privileged access abuse.
Cross-chain threat modeling & rollup security: With the growing popularity of rollups (Optimism, Arbitrum, zkSync) and L2 networks, future CEXs will have to include multi-chain threat detection tools, fraud-proof monitoring, and bridging protocol audits in their multi-layered security design.
In this new world, layered defense’s future is modularity, automation, and real-time response to move beyond passive controls to predictive, adaptive models. These models will be capable of keeping pace with the innovation of attackers.
Wrapping up
Centralized exchanges are prime targets for many hackers, so protecting them requires more than excellent code or basic authentication. It demands a tightly integrated, multi-layered security infrastructure that integrates infrastructure hardening, key management, identity control, monitoring, and compliance.
Applying and maintaining that infrastructure in-house is not just challenging — it’s time- and resource-intensive. That’s where we come in.
If you’re looking to launch a scalable and compliant CEX with robust security features, contact us today. You will get a white-label solution with which you can enter the market in weeks!
FAQ
It is a powerful protection system that employs independent security controls across various layers (user, application, network, data). Applying this approach, you will reduce the probability of a breach due to a single point of failure.
Identity and access management (IAM), application and runtime protection, wallet-level protection (HSMs/MPC), network segmentation, monitoring, and compliance enforcement are major elements.
Enhanced attack resistance, stronger protection of user assets, and dynamic risk management — all these factors are foundational to user confidence and regulatory compliance.
MPC (multi-party computation) eliminates single points of failure by distributing control of private keys across multiple parties so that transactions can be signed securely without exposing full keys, ideal for custody and withdrawal procedures.