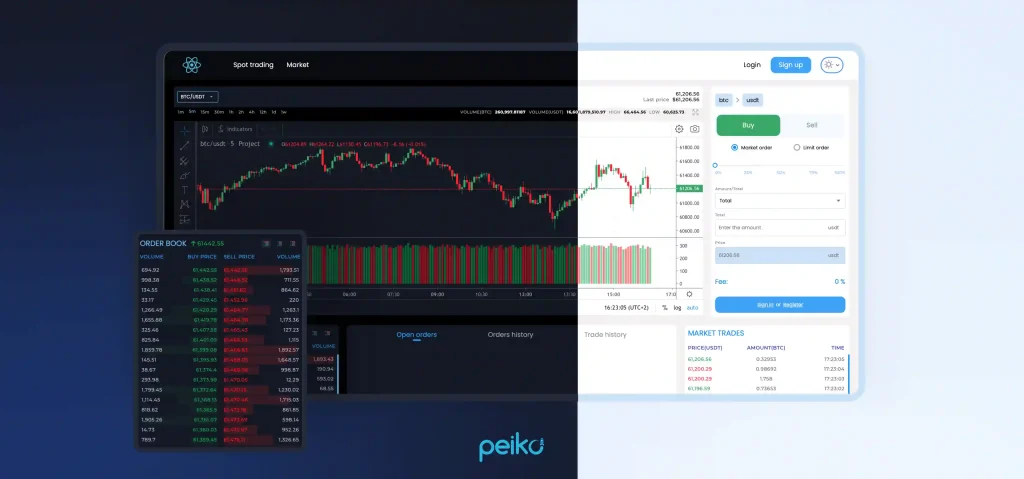
What is a crypto exchange engine, and how is it used? A cryptocurrency exchange engine is software that regulates all operations for interacting with coins and tokens. In this article, we will analyze this important component of every crypto exchange in more detail.
What is a crypto exchange engine?
Surely, you’ve seen the “top sales” or “recommended” sections on online store pages. Such lists are produced by analyzing transaction data, comparing product ratings, and calculating order volume. A crypto exchange engine works similarly. Without it, platforms can’t process orders or maintain real-time markets.
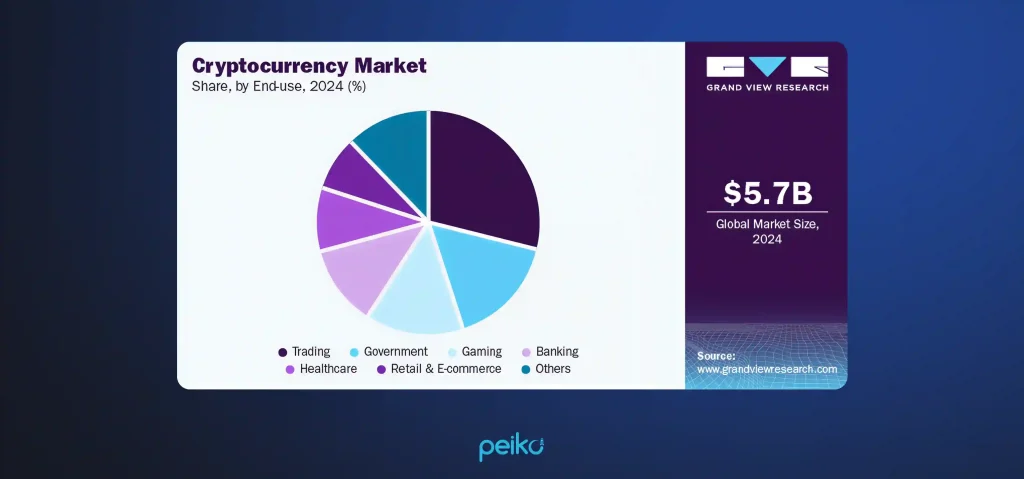
The global cryptocurrency industry was valued at $5.70 billion in 2024 and is expected to increase to $11.71 billion by 2030, with a CAGR of 13.1% between 2025 and 2030. Exchange software had the biggest market share in 2024.
The development of software to manage the massive amounts of data generated by cryptocurrencies is expected to drive the segment’s growth by 2029. Furthermore, the expanding global demand for cryptocurrencies will increase the demand for crypto wallets and exchange software.
If you plan to implement crypto services or build a crypto exchange platform, trust the execution to experts with cryptocurrency development services by Peiko.
How does the matching engine work?
So, let’s discuss how crypto exchange engines work. Before the assets are bought, the engine identifies matching sell orders. Later, when a buyer places an order, the system finds a seller with compatible terms. Each transaction includes protocols and order types that contribute to transparency, liquidity, and security. The engine also manages their processing and analytics.
Bid-ask spreads power crypto exchanges. Sellers want higher prices, buyers want lower ones – this difference creates the spread. Crypto exchanges profit from these spreads while their matching engines work to narrow them. Tighter spreads mean better liquidity and more efficient markets.
Types of exchanges that use a cryptocurrency exchange engine
Therefore, crypto developers should be aware of each type of crypto exchange to create a robust trading engine. Based on security factors and components (smart protocols, KYC/AML, money transmitter licenses, etc.), all types of cryptocurrency exchanges can be classified into these categories:
- Centralized exchange (CEX). Most common, like OKX or Coinbase. Offers high liquidity and user-friendliness but requires regulatory compliance and server-side security.
- Decentralized exchange (DEX). Peer-to-peer (P2P) trades without intermediaries. Prioritizes privacy and transparency.
- Hybrid exchange (HEX). Combines the speed of CEX with the transparency of DEX.
CEX vs DEX engine models
Let’s consider the difference between the CEX and DEX engine models in the table below. You can see the pros and cons of each option.
| Engine models | Benefits | Drawbacks |
| CEX |
| |
| DEX |
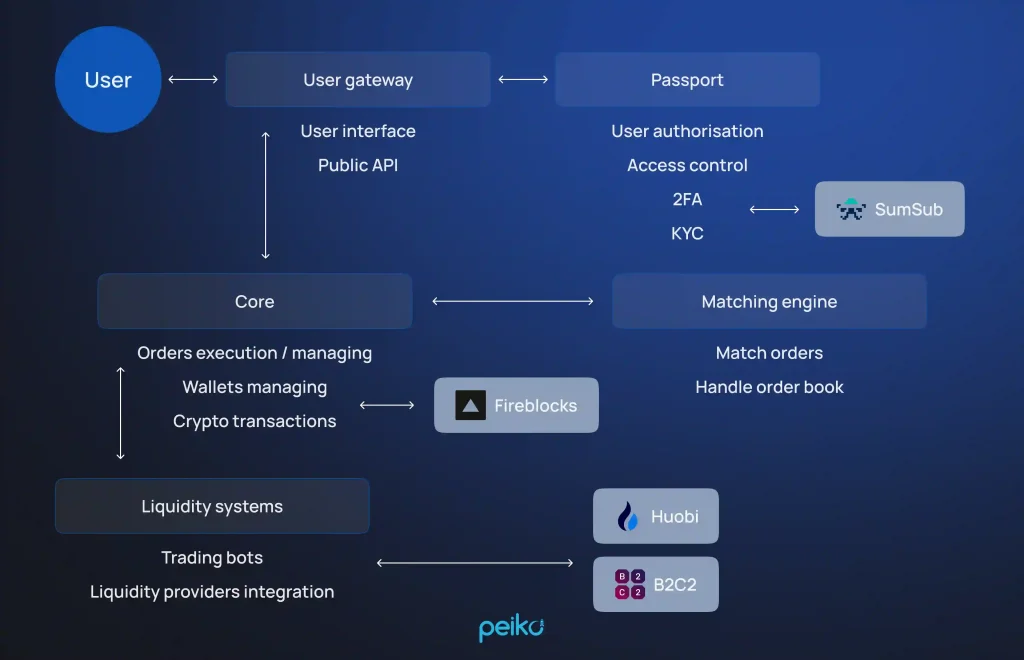
The CEX engines’ technological capabilities are represented in the functions of order matching in memory, Redis/PostgreSQL protocols for the registry/state, and a web API (REST/WebSocket) for trading. DEX engines typically appear in AMMs (Automated Market Makers) without an order book, utilizing liquidity pools, or in DEX order books with more advanced capabilities.
Main components of a crypto exchange engine
The crypto market engine goes through the same stages of production as assembly, testing, and programming. The engine serves as the foundation for everything from NFT gaming services to decentralized finance (DeFi) platforms and digital asset trading. The components of the crypto engine may vary depending on their operation. We will discuss them in this part.
Order matching engine
The cryptocurrency exchange matching engine is the heart of the order matching engine (OME). It filters the market, displays trading pairs (BTC/Solana or ETH/USDC), and provides the user with a list of brokers. Here’s how OME usually works:
- A new order is submitted through the trading interface or API;
- The engine searches the order book for compatible orders;
- If a match is found, the transaction is completed and documented;
- If a match isn’t found, the order will stay open until matched or cancelled.
The OME promotes fairness by prioritizing both price and time. The latency and speed of the matching engine have major implications for precise execution, particularly among high-volume traders.
Order book
An order book resembles a computerized catalog of all purchase and sell orders made on an exchange for a specific cryptocurrency pair, such as BTC/LTC or ETH/Solana. This list is regularly updated in real-time and reflects changes made when traders place new orders or cancel existing ones.
It performs the same role in a regular stock market, though it is especially pertinent in cryptocurrency due to the market’s relative volatility and 24-hour operation schedule. Each order in the order book contains pertinent details such as price and quantity (or volume).
Trade execution module
It is a required option for executing trades on the Solana blockchain or exchange. Market orders are commonly used to maintain sub-minute trading speeds. The trade execution module allows you to choose slippage tolerance (for example, 0.5% maximum slippage).
This component is responsible for executing trades on cryptocurrency exchanges based on indications provided by AI algorithms. It optimizes trade execution based on liquidity and transaction fees. In addition, error handling is dynamic. For example, a retry in the event of execution failure after repairing is unlikely.
Wallet system: cold wallets and hot wallets
Any cryptocurrency exchange platform is built around its wallet mechanism. It handles user deposits, withdrawals, and balance tracking for different coins and brokerage interactions.
When working with white-label solutions, wallet integration is often done by configuring pre-built modules instead of by scripting from zero. Hot wallets are used for rapid transactions. Otherwise, cold wallets are effective for storing a wide range of user assets completely offline.
| Type of wallet | The core pros | The main cons |
| Hot | Utilize firewall protection and continuous monitoring. | Limit balance thresholds to mitigate risks. |
| Cold | Place under strict physical security (safe storage with biometric access). | Only connect to the internet during specific periods (e.g., for large withdrawals). |
An efficient cryptocurrency wallet stores and manages the digital currencies on the exchange server while maintaining optimum security. To mitigate risk, each exchange platform must include both a hot and a cold crypto wallet mechanism. Integrating multi-signature cryptography settings in both hot and cold wallets enables traders to manage their KYC and AML checks while ensuring regulatory compliance.
User account management
Account management systems should be both user-friendly and secure. Users must be able to swiftly establish accounts or enable two-factor authentication (2FA), as well as manage their data. Second, the platform should have KYC/AML connectivity to demonstrate regulatory compliance and grow user trust.

Account management systems are one of several safeguards to protect your trading activities. However, if you overlook the risk of a hack, you will likely meet the same fate as Bybit. On February 21, 2025, hackers from the Lazarus Group compromised one of ByBit’s providers, stealthily changing the address of the digital wallet from which they delivered 401,000 ETH tokens.
According to Dr. Tom Robinson, co-founder of crypto research firm Elliptic, “Every minute counts for hackers who are attempting to obscure the money trail.” They know how to accomplish it. So it is the responsibility of exchanges and platforms to avoid this.”
Balance management
While we followed industry guidelines in our transition to microservices by attempting to develop autonomous, cohesive services with minimal dependencies on one another, the order service provider remained heavily reliant on numerous other areas of operations.
The Account Balance Management (ABM) service, performed by the credit check component of the order fulfillment flow, is an example of a self-contained component of a cryptocurrency exchange engine. Balance adjustments for a given account on the platform can occur for a variety of reasons and in various parts of the platform:
- Depositing tokens to your account,
- Withdrawing coins to your account,
- Trading and other exchange operations.
A service designed for multiple parallel ABMs enhances the platform’s scalability. For example, if one of the load alarms (CPU/HD) is triggered, the threads are dispersed in parallel to reduce the risk.
Market data feed
The market data stream offers the system the data required to make trading decisions. Examples include direct feeds from exchanges, consolidated feeds that combine information from multiple sources, and archive data sources used in backtesting.
The market data stream gives real-time or historical data to the system, which is then used to make trading decisions. The strategy engine uses this to generate trade alerts based on predefined parameters. The risk management system monitors the system’s performance and changes trading activity to mitigate risk. Finally, the order routing system performs trades on the relevant exchange or trading venue.
Security and risk engine
The risk engine is the stronghold that defends our exchange. Transactions do not get lost in our matching engine. The trade balance is never negative. All data is stored in memory, enabling extremely quick matching and response times. A write-ahead log and snapshotting guarantee data permanence and consistency, ensuring that orders are never lost.
The real-time audit risk engine follows the ACID framework (atomicity, consistency, isolation, and durability). To securely implement, exchanges typically use a Merkle tree structure, where each leaf node contains a hashed version of user balances (these endpoints form the cryptographic foundation of the verification system). This enables verification of the entire list of balances without compromising individual accounts.
Admin panel and monitoring tools
The administrative panel displays real-time data on traffic, trade volume, transactions, and commission income. You can track traders, wallets, and transactions while maintaining a safe trading environment. It enables you to perform major tasks such as user verification, content management, and account management. The admin panel’s versatility allows you to adjust fees to optimize income.
The admin panel should have KYC/AML modules, as well as reporting/analytics capabilities for monitoring compliance with a crypto exchange’s legal procedures. Some of these tools include the FCA as a regulating body and the MiCA rules. They are required to track Bitcoin transactions, verify operations, and manage risks.
Building or choosing a crypto trading engine
Creating your own software or choosing an existing one is a dilemma for businesses of any level. Foremost, this concerns the budget and functionality. Crypto trading engine explained through the number of tokens, user activity, and usage scope helps show how it works.
Annual subscriptions can cost about $10-20k. At the same time, custom crypto exchange engine software is more variable and allows you to adjust it to your needs. Their cost is indicated in the table below.
| Blockchain application | Components | Development price, $ |
| Low-cost | Basic smart contracts, P2P, simple exchange models, and an NFT marketplace. | 25000-60000 |
| Middle-cost | The architecture has centralized and decentralized segments (crypto-wallets, DEX, simple CEX, Layer-2 blockchains). | 60000-150000 |
| High-cost | Layer-1 blockchain, web3 trading technology, custom exchange system. | 150000-300000 |
Each blockchain system has its own consensus algorithm, like Bitcoin’s proof of work or Ethereum 2.0’s proof of stake. When the price for developing a CEX application is calculated, it is determined which mechanism is best, depending on your requirements. Other features to examine are user permissions, renewal mechanisms, asset issuance, key management and structure, signatures, and address formats.
How to pick the crypto market engine correctly?
First, we must determine the engine’s principal objective. At its core, it employs an order sorting mechanism, usually a price-time or First-In-First-Out (FIFO) model. That is, orders are matched first based on price, and afterward on submission time. In general, a high-performance trading engine is built to the following specifications.
- Select your exchange type. CEX is faster, feature-rich, but custodial. Otherwise, DEX is user-controlled, transparent, and slower.
- Match engine performance. For MVPs, use open-source engines (e.g., HollaEx, Peatio). For scaling, go for high-performance engines (C++/Go) with in-memory matching.
- Security and compliance. Must support KYC/AML, secure wallet integration, and audit trails — especially if you’re operating in regulated regions.
- APIs. Look for REST/WebSocket APIs, real-time order book, and historical trade data.
- Plan for scale. Pick an engine that handles high volume, multi-pair trading, and offers monitoring tools.
Some engines offer more complex order types and algorithms, such as iceberg (hiding huge orders), TWAP (evenly dispersing orders over time), or VWAP (buying or selling based on average price), depending on the platform’s requirements.
That’s why choosing a small-functioned open-source exchange engine is a good option if you’re testing the theme. On the other hand, consider customizing if you’re scaling rapidly or require regulatory compliance.
Hidden shields in the crypto exchange engine
To build a turnkey cryptocurrency exchange engine, an entrepreneur must use discrete, independent modules. Even if one of them fails, the system resumes normal operation thanks to these modules.
Some modules may be restricted owing to legislative activities surrounding crypto platforms in the nation. Cryptocurrency, for example, is officially allowed in Switzerland, although it is restricted in India and the United States. Creating a modular structure on your site can help optimize client work and maintain high-quality crypto exchange services.
Future of the crypto trading engines
The trendiness of a niche market is determined by the target audience and their needs. As for digital trading engine mechanics, Bitfinex & Tether CTO Paolo Ardoino answered this question in the info below.
It is simple to forecast patterns and upcoming developments in cryptocurrency exchange engine development. Incorporating SaaS into your exchange will matter in 2025, and firms that recognize the validator, custody, and disclosure stack early on will secure income streams that can endure the next bear market. The following trends are going to persist over the next five years.
- Support for staking operations will be integrated directly into the exchange engine Allowing platforms to offer native yield-generating services without relying on external protocols.
- Engine-level compliance modules will become standard Enabling exchanges to adapt more easily to evolving licensing requirements in the EU, US, and Asia-Pacific jurisdictions.
- Validator and node orchestration will be optimized at the engine layer Increasing performance and minimizing latency for networks that rely on proof-of-stake consensus — especially in hybrid exchange setups.
Staking functionality is now deeply integrated into the crypto exchange engine itself, no longer operating as a standalone product under the “Earn” section. With Proof-of-Stake (PoS) rewards driving over $140 billion in revenue, about 7% of the total crypto market cap, modern Tier-1 exchange engines are being re-architected to natively support staking operations, validator coordination, and automated yield distribution as part of their core logic.
Blockchain technology is transforming the power trading scene by bringing transparency and efficiency. As an integral component of energy innovation, blockchain-enabled electricity trading empowers both consumers and producers, enabling a dynamic and sustainable energy economy. Blockchain and energy systems give consumers more control over their electricity, especially up to a 40% reduction in regular data.
Step forward to the crypto exchanges with a strapping trading engine
Are you interested in cryptocurrencies and their operations? Want to create your own platform with great functionality? Our white-label exchange platform features a robust, pre-integrated trading engine optimized for real-time processing and swift order execution.
You can build a fully functional centralized exchange (CEX) in as little as three weeks, eliminating the need for familiarity with technical specifics from the outset. The platform can quickly scale to handle enormous volumes of processes; therefore, there will be no platform overload or stutter. Experienced merchants and retail clients will be eager to participate in such an environment.
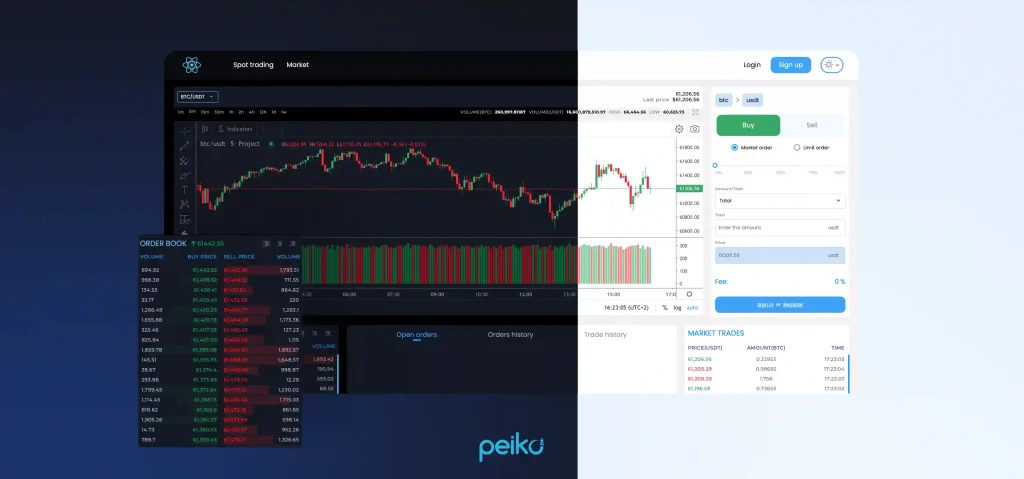
TradingView’s patented charting, automated order matching, and ready-made liquidity ensure that your platform is operational from the start. With our robust infrastructure and expert blockchain professionals, you can go live faster, scale up easily, and begin earning money sooner!
Pick up the crypto engine development with Peiko
Crypto exchange engine processes various types of requests. Transaction limiting, entering restrictions, and checking verification are a small part of the multibyte data flow. Contact us, and you will get the software you need. Our team implements CEX development, white-label exchange service development, and other services in the field of blockchain technologies.
FAQ
A blockchain engine is the software that powers decentralized applications, handling smart contracts, transactions, and consensus.
Yes, crypto exchanges are widely used globally for trading digital assets — both centralized (like Binance) and decentralized (like Uniswap).
Coinbase is considered one of the most legitimate due to its U.S. regulation, transparency, and strong security practices. Otherwise, you should review local platforms.
Look for poor grammar, lack of HTTPS, fake reviews, missing legal information, and verify the domain against the official project site.
It can add transparency, automate trust via smart contracts, reduce intermediaries, and supply secure peer-to-peer transactions.